This document is a summary of selected PCRecruiter infrastructure, security, and availability items. For specific product feature questions, detailed vendor assessment / document packages, or other control objective information, please see www.pcrecruiter.net, or please contact a Main Sequence sales consultant.
Physical / Infrastructure
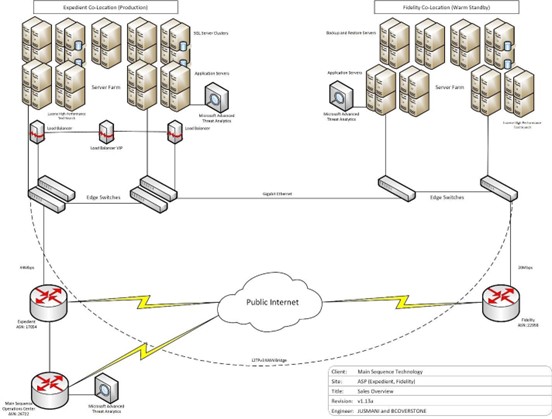
Main Sequence maintains private cloud hosting for PCRecruiter SaaS, comprised of three physical sites. From time to time, backup data may be moved to additional company designated sites for safe long-term storage. The two primary hosting facilities are the Expedient, Inc. co-location facility located in Northeast Ohio (postal code 44128), and the Fidelity Inc. co-location facility located in Northeast Ohio (postal code 44115). The two facilities are separated by more than 25KM. Fidelity is designated as the warm-standby center, but is managed in all other respects as a primary datacenter. Fidelity hosted PCRecruiter accounts are available in read-only status and designated as the PCRecruiter “Snapshot” feature.
Primary datacenters are protected by items including, but not limited to: 24-hour guard; video monitoring, access logging, and strict enforcement of escort and access rules. To enter facilities, a person must be in possession of an Expedient or Fidelity key pass, which may only be arranged for via prior filing of government issued ID, and requiring the express permission of Main Sequence for each visit and visitor. Data-center entrances are physically guarded 24/7. All equipment is caged. Within hosting facilities, customer data is stored in multiple locations. Main Sequence policy requires not fewer than three complete copies of customer data maintained on fully independent media at all times. These media may include RAID/SAN networks, hard disc drives, and solid-state devices.
A third location where account data may be located is a Main Sequence operations facility separated by approx. 50KM from the primary data center(s). Physical security is similar to the primary hosting sites, including but not limited to: controlled, escorted access by prior arrangement, telecom quality power, environmental controls, video surveillance, and 24 hour technical support/monitoring. The operations site is used for utility activates including, but not limited to: hosting of data conversion projects, account mockups and other non-account data, remote management of datacenter assets and customer business information not generated by customer account activity. No active PCRecruiter accounts are hosted at this operations facility. Please see the included Network Diagram for an overview of PCRecruiter account hosting infrastructure.
People
Only senior technical personnel at Main Sequence may physically or electronically access the hosting infrastructure. Only senior technical personnel at Main Sequence may access customer data for technical support purposes. All Main Sequence personnel are bound to the confidentiality requirements of customer Service Agreements. All Main Sequence personnel undergo background checks prior to being granted access to customer data. Main Sequence conducts regular training and assessment of senior technical personnel specifically focused on maintaining the security and confidentiality of customer data. If any third party requires temporary access to customer data for technical reasons, all such parties must execute a comprehensive nondisclosure agreement, with all activity monitored by Main Sequence at all times.
Main Sequence offers professional services for application support, user education, compliance, and other related domains associated with the use of solutions provided by the company. Services are delivered and monitored by an online ticketing and tracking system.
Software
Application / Database Design
PCRecruiter offers several inherent security features. The application is composed of discrete modules. Each module is typically associated with a feature set, thereby limiting opportunity for malformed URL or overrun exploits being useful to intruders, as the compromised modules are limited by distribution to a hardware load-balanced server pool and are terminated by webserver(s) after execution. Modules also make use of thread priority coding to ensure that any failure or error in individual execution of PCRecruiter functions will not compromise the application webserver(s). PCRecruiter uses the latest Microsoft-based development tools and integrated development environment. The use of managed code via proprietary methods is a benefit because Windows Server components are considered secure and updated continuously by Microsoft to remain secure.
Within the application, each end-user has factored authentication and a complete security profile. Administrators may tailor their permissions to their role. The application maintains SQL Server database connection information in encrypted files. A public key/private key security feature is available for individual database fields as needed for information classified at higher levels. All passwords are transmitted via SSL regardless of URL prefix. Users have options to encrypt fields when required for legal or operational purposes.
Internal Network
The Main Sequence service network is a combined LAN/WAN composed of, but not limited to: a load balanced group of application servers, redundant routers and switches, storage devices, database server clusters, and various software components. Redundant Cisco routers and switches manage IP translation. Application services are transacted through redundant hardware load balancers and WAF’s to translate and obscure individual IP addresses and balance IP requests. Main Sequence monitors Microsoft’s IIS, SQL Server, and Windows support Websites to ensure that all systems are promptly and fully patched for critical security issues. Outside security organizations are regularly contracted with to perform assessments and penetration testing against the network and software code. NAGIOS network monitoring is customized and enabled for all key services and components, including power switching and database health.
Procedures
Customer accounts do not share non-anonymized database tables with any other customer, to minimize the chances of SQL syntax errors or successful exploits exposing customer data to other customers, to reduce the possibility of errors in data return, to better monitor customer usage and performance, to help assure rapid field installation of data, and to provide more fault tolerance via decentralization (so that database errors or performance issues could less easily affect multiple customers)
Each SQL Server database is optimized and managed by Microsoft System agent, to assure restorable backup files and planned performance. Each database is secured on the user account and password level. Each database is monitored for size, growth rate, remaining storage, and error events. Databases are most often held on dedicated clusters of Windows servers.
Backups are AES 256 encrypted and are typically maintained in two or more sets for disaster recovery and operational recovery. RTO is zero minutes for total data center loss. A read-only version of customer accounts with the most-recent backup is maintained at all times as a warm standby at the secondary data center and may be accessed by customers at any time by placing the word “snapshot.” as a prefix to the account URL. RPO is 0 to 6 hours for a total data center loss. Backup data is moved incrementally electronically offsite using a dedicated peered Internet circuit on Main Sequence’s BGP mesh network, executed by an extensively optimized scripted process.
Public Network Communications
Main Sequence maintains multiple independent Internet circuits using BGP routing and a public, Main Sequence-owned Autonomous System Number (ASN,) assuring that the Main Sequence network is discrete from its network carriers (requiring no third-party permission to establish routing) or any other single point of network failure. All customer data is encrypted via TLS/SSL. Bandwidth monitoring and intrusion detection systems are in place. Main Sequence adds bandwidth when steady usage exceeds 50% of any circuit’s capacity.
Servers
Main Sequence uses whitebox or branded Windows servers with branded components. (Intel and AMD CPU’s, Seagate, IBM , and WDC Storage, Micron memory, Intel server boards, etc.). Main Sequence installs all software in house, starting with completely unformatted volumes. All Web services except DNS, HTTP and SMTP are disabled and all TCP/IP ports except 80 are closed (with the exception of utility software, when ports are opened and closed for its use). Servers have redundant power supplies and onboard monitoring of environment, warnings, etc. Main Sequence senior technical personnel monitor the complete health, patch status, and privilege/access situation of all servers on a continuous basis. A multiple-sensed automated test and performance suite contacts technical personnel by cell phone, email, and SMS when trouble is detected with any host. Servers are load balanced and no customer is limited to a single server unless specifically arranged by request.
Power
In addition to facility power, critical Main Sequence equipment is connected to Compaq Digital Signal Processor Uninterruptible Power Supplies for overvolt and undervolt protection and power conditioning. The data facilities are also key telecommunications interconnection sites and are powered externally by generators in the event of any long-term power disruption.
Integration
Main Sequence provides data return options including file delivery, XML In / Out, custom report engine w/ CSV exporter, and Rollup List functionality within the application (a rollup list allows end-users to group and format datasets for use in various ways). Main Sequence provides a fully featured API for third-party application integration using governance services provided by 3Scale Inc.
Monitoring and Assessment
Main Sequence contracts with various outside security vendors from time to time for non-baseline network and software code security workups. Tools used include Nessus, (a vulnerability scanning tool), and Nmap (a port-scanning and host identification tool) as well as other proprietary methods used to stress test the service. Bandwidth usage is monitored and any spikes or unusual use patterns are tracked (to prevent and identify denial of service attacks (DoS or DDoS)) as well as to detect and prevent any unauthorized use of Main Sequence assets. Snort IDS is used for intrusion detection. All identified security events or threats are rated for severity and required policy response. Any identified security vulnerability that results in a “high” or “critical” rating is remedied at the earliest practicable time following discovery. Expert recommendations of changes to the network and any threat labeled “medium” are discussed and logged to the operations documentation. Software analysis, penetration testing, and security process training and monitoring is provided at least annually. Main Sequence’s multiyear vendor for these baseline services is RSM US, LLP
Legal / Regulatory
Unless otherwise indicated in a customer Usage Agreement, all customer data at all times remains the exclusive property of the customer. Main Sequence has no rights whatsoever to use, disclose, sell, publish, or otherwise derive any benefit of any kind from non-anonymized customer data, with the exception that Main Sequence may query and analyze data for technical support purposes. Main Sequence provides complete confidentiality language in User Agreements and Software Licenses. Main Sequence is the party contracting for services directly with its telecom hosting providers, maintaining its accounts to current status at all times, and no Main Sequence equipment or provisions are potentially subject to creditor actions or claims of any nature.
PCRecruiter SaaS customers may license materially similar software for use on their own equipment, subject to the terms of a Software License Agreement. SaaS customers are required to execute a Usage and Fee Agreement with Main Sequence detailing information regarding the relevant terms and conditions relating to Main Sequence solutions. Main Sequence negotiates individual SLA terms and conditions with customers based on their requirements, including the provision of program object code, documentation and customer-data as needed.
The security of customer data is an overriding objective in every business decision and project undertaken. Because customer data may be connected directly to the public Internet, there remains, and will remain a possibility of security or denial of service issues arising.
Main Sequence does not assume liability for data loss or security breach. The Main Sequence Usage Agreement inter alia specifically releases Main Sequence against damages for loss of data, security violations, and special, punitive, or consequential damages of any kind.
Main Sequence is committed to a commercially high standard of security and continuous network availability, intending to operate the service using security, access, and availability standards and policies that are representative of practices and policies prevailing in the industry as offered by other vendors of similar services at similar times.
Network Diagram
The information contained in this document is provided by Main Sequence as of the date of publication. This information is not a promise, inducement, or guarantee. This document is not a warranty of any kind, neither express nor implied, including but not limited to suggesting merchantability; fitness for a particular purpose; or any guarantee of timeliness, accuracy or performance; any acts or omissions of third-parties; any losses or damages due to force majeure; any losses or damages due to ordinary negligence against which a party may be insured; or any form of indirect, consequential, or special damages.
